In recent years a new security concept has made the headlines - two-step verification or two-factor authentication (2FA). It all started with Google enabling it for its users, and since then, many companies followed their example, including Microsoft, Apple, and Facebook. Even gaming companies joined this trend. If you would like to understand what two-factor authentication is, how it works, why you should enable it and where read this article:
What is two-step authentication or verification?
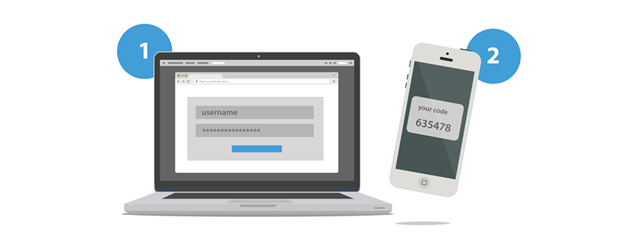
Two-factor authentication is a security process that involves two stages for verifying the identity of a person or entity that is trying to access a service of any kind (e-mail, social networking, banking, etc.). This concept is also named two-step verification, and it requires two or more of these three authentication factors: a knowledge factor, a possession factor, and an inherence factor.
Traditional authentication involves only one or two of the three factors mentioned earlier. For example, if you want to use a service like e-mail, traditional authentication involves knowing a username and its password. Knowledge can be stolen in a variety of ways and people can find out both your username and password, and then use that information to pose as you, or steal valuable information that can be used to harm you.
In the real world, traditional verification may involve the knowledge factor and the possession factor. For example, when you go to an ATM to get cash, you use your debit or credit card (possession factor) and the PIN (a knowledge factor). However, both the PIN or the information on your credit card can be stolen in various ways, and unauthorized parties can make online transactions using your money. That's why the 3D Secure concept has been developed to provide an additional security layer for online credit and debit card transactions.
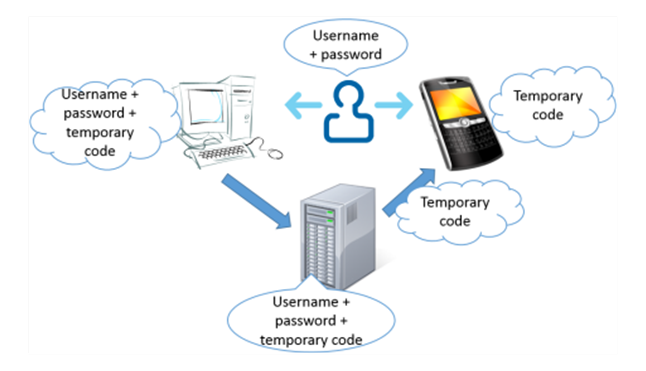
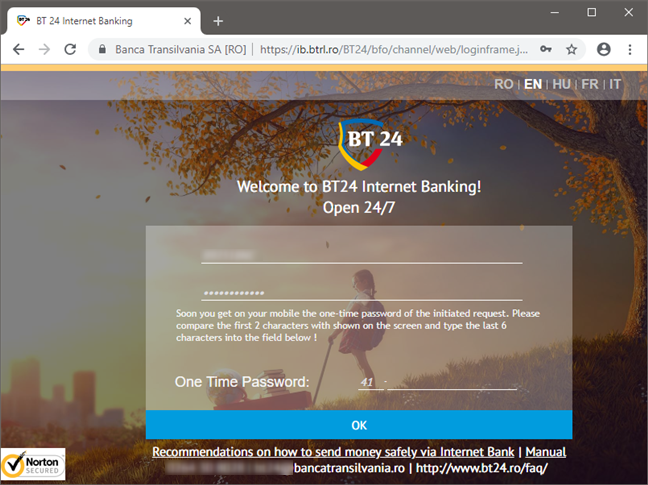
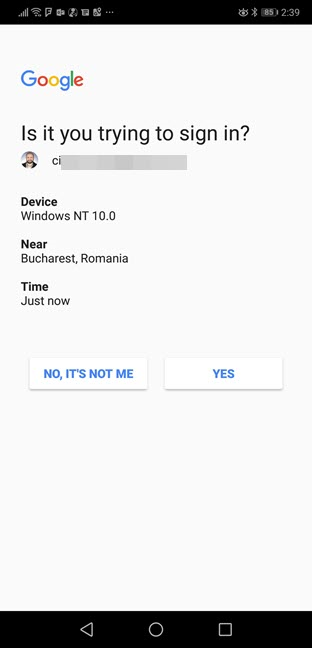
When using two-step verification in the digital world, a third factor is added: the possession factor - usually your smartphone or mobile phone. This device is used for the second stage of verifying your identity. For example, when you sign-in to your email account, you first provide your username and password. Then, you are asked to provide a time-based password that expires in a couple of seconds. This password can be sent to your email account, to your smartphone, or it can be generated by an authenticator app such as Google Authenticator or Microsoft Authenticator.
Some companies and services also provide physical authentication devices that continuously generate the codes you need to use to finalize the verification process. For example, many banks provide physical devices for two-step verification, so that you can access your bank account online. Also, PayPal does this for a number of countries, including the USA.
How does two-factor authentication work?
The implementations for two-step authentication are many, and we do not go into details about all of them because this article would become very long.
The most popular implementation is Google's approach based on the TOTP - Time-based One-time Password Algorithm. When two-step verification is enabled for your account, a special server generates a new password/code once every couple of seconds. The device sharing the password with you needs to be synchronized with the server so that the code you enter during the second authentication step matches the one on the server. If the device sharing the password is out of sync, you cannot complete the verification of your identity.
This algorithm is the most popular one found online. Many companies use it, including Google, Microsoft, Apple, Facebook, Evernote, Dropbox, WordPress, MailChimp, and LastPass.
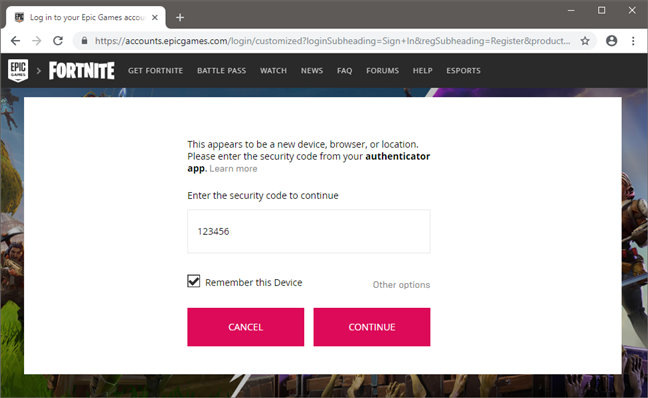
To make it easier for you to understand how two-factor authentication works, let's take for example Fortnite, a popular online game that many people play. Once you have configured two-factor authentication (2FA) for your Epic Games account (the creators of Fortnite), it is no longer enough just to provide your username and password to log in. You also have to provide a secondary passcode to be able to do that.
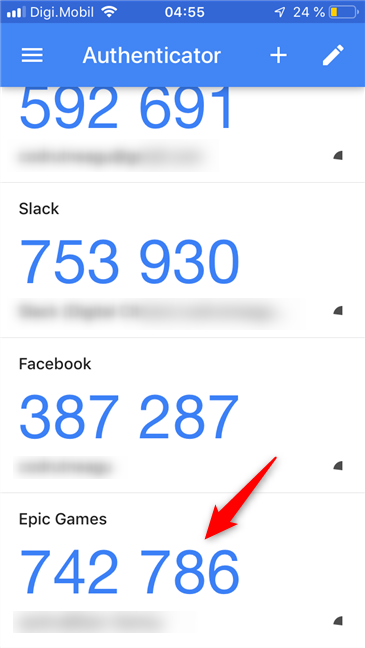
The additional passcode is temporary, and you are the only one who knows it. No one else should be able to find it, as you can only get this code from an authenticator app (such as Google Authenticator) or from an email message you receive from Epic Games. The two-factor authentication codes change every couple of seconds, so they should be almost impossible to guess.
If you provide the correct two-factor authentication code, you are signed into your Fortnite account. For the next 30 days, you do not have to provide 2FA codes on the device on which you already signed in. However, at the end of the 30 days or if you try to log in from a new device, you have to provide a valid 2FA passcode again.
Two-factor authentication in the banking sector
Another popular approach is the one used by banks and credit card providers. It is named 3-D Secure, and it is used for approving financial transactions that are made online. This method of two-step verification involves three entities: the domain of the merchant or the bank to which the money is being paid, the domain of the bank which issues the card being used and the infrastructure that supports the 3-D protocol.
This protocol uses only secure SSL connections for making online transactions and, for a transaction to be approved, you need a special password, alongside your name and credit card details. This password may be temporary and time-based, or it may be permanent and set by you, the user. Another important aspect is that this password is not stored by the merchant or the bank to which money is being paid. The password is known only by the servers providing the infrastructure for the 3-D protocol. Therefore, if the merchant is hacked, hackers cannot get your 3-D Secure password.
Why do you need two-factor authentication?
The main reason why you should use two-step verification is to protect yourself. By using this additional layer of protection, you make it harder for unwanted parties to access your identity online and steal personal or financial data.
When using 3-D Secure for financial transactions, you make it harder for hackers to steal your money. It is easy for them to copy your card details but they are going to have a hard time getting your 3-D Secure password.
When should you use two-factor authentication?
Adding a secondary authentication step is annoying for everyone but necessary to keep our accounts and data private. We highly recommend that you enable and use two-step verification at least for the following types of services:
- E-mail - your Inbox stores the biggest amount of personal data out of all your online accounts. People can spy on your email history, learn the username for your banking and PayPal accounts, learn more about your work, your relationships, and many other important details. Securing your inbox is the first thing you should do.
- Online banking & financial transactions - if you do online banking, if you purchase stuff from Amazon, eBay or other online shops, you must secure your credit or debit card. Ask your bank about 3-D secure and the two-step verification options they offer, enable them and use them.
- Storing your passwords - many security conscious people use services like LastPass, Roboform or KeePass. Securing them is crucial. If your account password is stolen, unauthorized parties have access to all your passwords and can do a lot of harm to you.
- Social Networking - we all store lots of personal data on social networks such as Facebook, Twitter, or Instagram. If others get access to your data, they might find many things you would rather keep private. For example, if you have a jealous partner, they may already know your Facebook password and keep an eye on what you do. Protect yourself and enable two-factor authentication.
How to enable two-factor authentication for your most important accounts
In general, enabling two-factor authentication means that you have to log in to your online account and head to your password and security settings. Then, if you can use two-factor authentication for your account, you should find an option for it. If 2FA is available, enabling it means following a couple of steps in which you choose the method you prefer (usually, that is authentication via email or authenticator app on a smartphone). To help you out in enabling and using two-factor authentication, we have published a few guides that cover some of the most popular online services:
- How to enable or disable 2-step verification for your Google account
- Approve or deny sign-in requests to your Microsoft account using Android
- How to activate two-step verification for your Apple ID, on an iPhone or iPad
- Set up two-step verification for your Microsoft account with Google Authenticator
- How to enable and use Fortnite's 2FA (two-factor authentication)
- Enable and use two-factor authentication (2FA) for your Blizzard account
Also, if you are looking for an easy way to implement two-factor authentication in your own company, here is a short article about the benefits of an excellent solution of this kind: 7 things you can do with ESET Secure Authentication.
Have you enabled two-factor authentication on all your accounts?
We hope that you found this guide useful. If you have any questions or issues with understanding how two-step verification works, do not hesitate to leave a comment below.


 27.11.2018
27.11.2018