Key reinstallation attacks or KRACK are cyberattacks that exploit a vulnerability in the way WiFi networks encrypt and transmit data, with the aim of stealing what is transmitted over the network. Such attacks can result in theft of sensitive information or can be used as man-in-the-middle attacks, serving the victim a fake website or injecting malicious code into a legitimate site. Recently, researchers from ESET have revealed that some Echo and Kindle devices from Amazon are vulnerable to this attack. Here is what this means, why IoT devices are attacked, and how to prevent attacks in your home or business:
Amazon's Echo and the 8th generation of Amazon Kindle are vulnerable to KRACK attacks
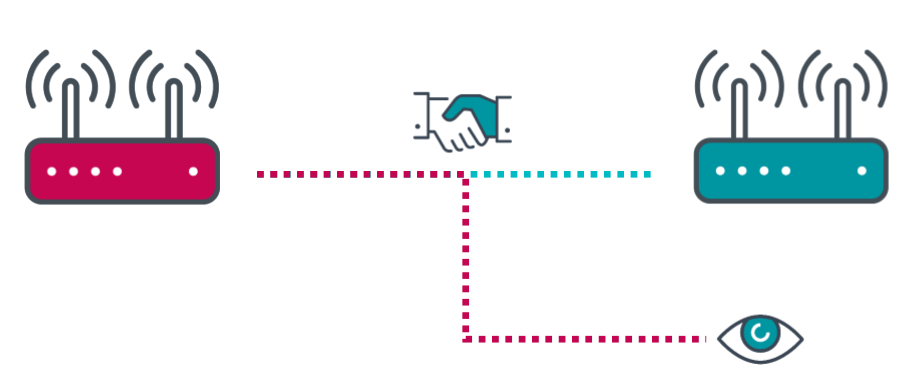
According to research from ESET's Smart Home Research Team, the first generation of Amazon Echo devices (released in 2015), and the 8th generation of Kindle (released in 2016) are vulnerable to the KRACK attack, which made the headlines in 2017. It is a significant vulnerability that affected all WiFi networks, and allowed attackers to decrypt all the data that their victims transmit, and use it as they see fit.
Because of this vulnerability, unpatched Amazon Echo and Kindle devices could have their communication decrypted, data could be injected and forged, and sensitive information could be exposed to the attacker.
ESET communicated this problem to Amazon in October 2018, and, in January 2019, Amazon confirmed that they could replicate the issue, and started to work on a patch. In the coming weeks, Amazon has also released new firmware updates for the vulnerable devices, to fix the problem. Therefore, if you have an Echo device, Check & Update Your Alexa Device Software. If you have an 8th generation Kindle, go to Kindle E-Reader Software Updates.
Why hackers love to target IoT devices like Amazon Echo
Amazon Echo is an IoT (Internet of Things) device that's popular in modern homes and businesses. People use it for many reasons, including for controlling other IoT devices in their homes, like their wireless routers, smart bulbs, smart plugs, sensors, thermostats, and so on. Echo is used to interact with Amazon's Alexa, which has more than 100,000 skills and growing. With its help, you can do things like order pizza, stream TV to a compatible device in your home, manage your to-do list, get the latest news, or control your Nest Learning Thermostat.
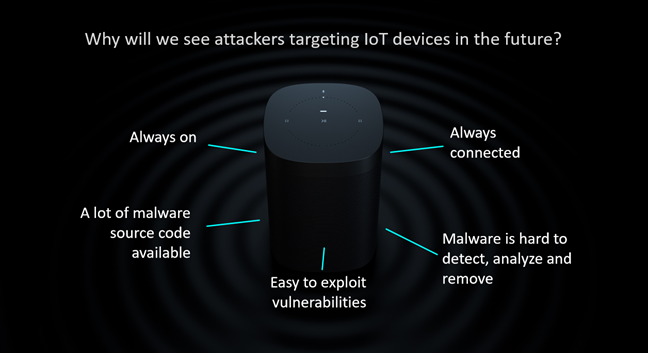
Amazon Echo and all other IoT devices share the following characteristics that make them appealing to attackers:
- Always on - you do not turn your Amazon Echo or your smart plug off. It is always turned on and waiting for your commands. So are all other IoT devices in your home or business.
- Always connected - your IoT devices are always connected to the WiFi, and often, also to the internet.
- Easy to exploit vulnerabilities - this is true, especially for cheaper devices, whose manufacturers did not invest a lot into security. Some IoT devices barely get firmware updates and security fixes.
- Malware is hard to detect, analyze, and remove - when an IoT device is compromised by an attacker, you may not notice unless you have the necessary tools to analyze the network traffic generated by that device. Furthermore, when an infection is detected, removing it is difficult if you do not possess the technical skills and tools necessary.
- A lot of malware source code available - it is easy to find both source code and tools that take advantage of known vulnerabilities for IoT devices. They are also effective because many IoT devices do not get updated regularly.
All these reasons make IoT devices an appealing target for hackers and attackers worldwide.
How to prevent attacks and protect your IoT devices
There is no "silver bullet" that can protect your IoT devices from all threats. However, there are some things you should do to increase security, and lower the success chance of an attack:
- If you can enjoy the benefits of using an IoT device, without connecting it directly to the internet, and only to your network, cut its internet access. This would significantly lower the chances of that IoT device becoming the victim of an attack.
- Use strong, unique passwords for all your IoT devices, as well as two-step authentication when available.
- Regularly update the firmware of your IoT devices. Many of them do not offer proactive alerts about firmware updates, so you have to create a habit of manually checking for updates once in a while.
- Enable encryption for network communication. Set your IoT devices to use HTTPS - the secure version of HTTP - so that their network traffic is encrypted. Therefore, even if the packets are sniffed or otherwise intercepted, they would come across as nonsensical characters.
- Disable unused services. Amazon's Echo and Alexa are perfect examples of smart IoT devices that have many skills and services. While this makes them useful, it also increases the attack surface. Therefore, if you are not using specific features (or skills) of an IoT device, disable them if you can, so that they cannot be used by an attacker.
- Use a wireless router with built-in security - some wireless routers include both an antivirus and intrusion prevention system, which makes it difficult for external attackers to compromise the network and the IoT devices that are connected to it. Also, if they do manage to compromise an IoT device, your wireless router can signal this problem, so that you can take action to fix it.
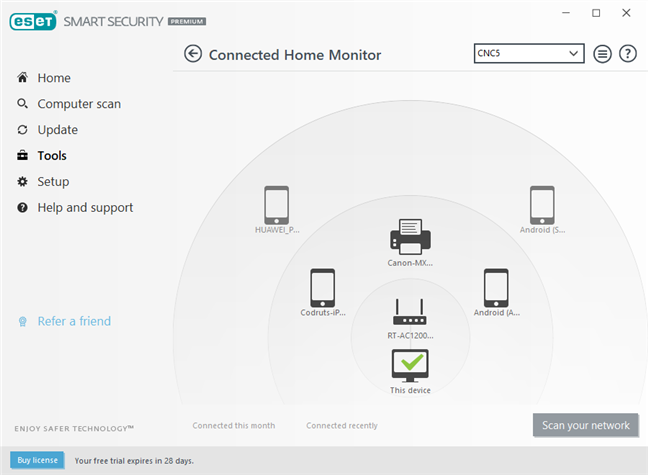
- Use an advanced security product that scans the devices in your network and evaluates their security. For example, ESET Smart Security Premium has a feature called Connected Home Monitor, which assesses the security of your network, identifies compromised devices, and gives you tips on improving safety.
How do you protect the IoT devices in your home or business?
The problems revealed by ESET about Amazon Echo and Kindle showcase how vulnerable IoT devices are. Yes, they are useful and make our life easier, but they are also an attack vector that is tempting to hackers and malware creators. Before closing, tell us what you think about what was revealed by ESET and how you protect the devices in your network. Comment below, and let's discuss.


 18.10.2019
18.10.2019