Do you have a girlfriend who has trust issues? Or a parent who acts a bit paranoid when he or she sees you spending most of your evenings chatting on your computer? The chance is that anyone close to you who has some computer skills, can spy on your Windows computer. Maybe they do that with good intentions (for example, you parent wants to make sure that you don't access content that is not appropriate for your age) or maybe your girlfriend is jealous and thinks you're cheating on her. If someone wants to spy on your computer, they will probably find a way to do it. Technology evolved so much that having your computer spied upon is not something out of the ordinary these days. We thought it would be a good idea for us to share some of the most common ways in which someone can spy on your Windows computer. Here they are:
1. Spying with remote desktop sharing tools
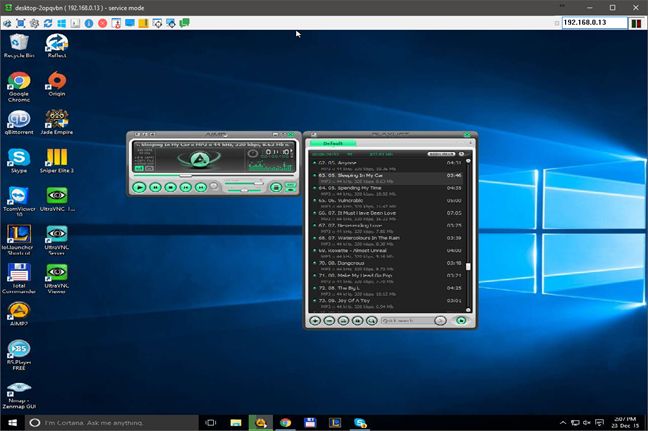
One of the easiest and simplest methods of spying on someone's computer is to use remote desktop tools. We're not talking about the Remote Desktop Connection tool found in all modern Windows systems. This tool would do fine for spying, but there is a problem: whenever a spy tried to use Remote Desktop Connection , your computer's screen would go blank and you would know that the other person has connected.
A wannabe spy could use third party tools that allow remote desktop connections while not letting you know about it. There are plenty of such programs out there, most of them being developed with good intentions, for legitimate purposes. A simple Google or Bing search will give you plenty of results with silent remote desktop tools like UltraVNC or RealVNC.
A spy can use any of these tools to watch your desktop, access your webcam and see everything you do or turn on your microphone and hear everything you say. He or she would have access to everything on your computer. Most of these apps can be set to start with Windows and work as a Windows service, so each time you'd open your computer, the spy would gain unattended access to it.
2. Spying with RATs (Remote Administration Tools/Trojans)
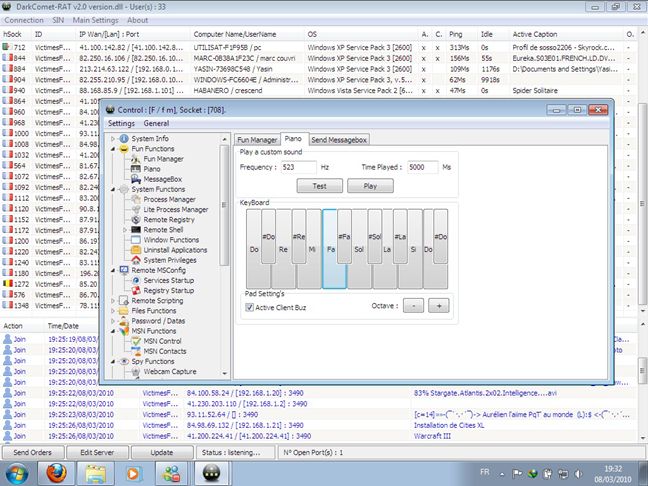
Spying with remote desktop sharing tools works, but it's mostly a rookie's way of doing business. The "professional" way of spying on someone's computer is to use RAT software. And we're not talking about the pesky rodents, even if there are lots of common features between them. RAT comes from Remote Administration Tools and it refers to software apps specially designed to allow the spy to control a computer without having physical access to it. RATs are tools that are hidden from the user's view and, if they are good, they are also stealthed from common antivirus software.
RATs allow spies to capture images from your screen and webcam, manage (copy, delete, run) the files found on your computer and so on. A spy can even overclock your hardware to the point of destruction, if that's what he or she wants.
Such desktop apps are usually distributed in the form of malicious trojan horse malware and are usually detected by antiviruses. However, many hackers appear to be using additional software that cloaks them and tricks average antivirus engines into thinking that they are safe. You're probably wondering how to get rid of such nasty malware in case you fall prey to it. The answer is simple: use very good antimalware software like what we recommend in our series of security reviews.
Source: Wikipedia.
RATs have been with us for as early as 1998, but it was the last decade that made them grow in popularity. There are people that use these tools to create lists of "slaves". The "slaves" are real people that don't know that they have a RAT on their computers and are constantly being spied on by the "masters". There are entire hacking forums dedicated to this business and "slaves" are even sold for a few bucks. Not using good antivirus software and falling victim to a RAT means you won't even know that you are being a slave and that someone is watching you whenever he or she wants.
RATs have become so popular that they are even being used by military agencies. A notable example is the Syrian government which used to use (and maybe still is) Blackshades and DarkComet in order to spy on their own citizens.
3 . Spying with keyloggers
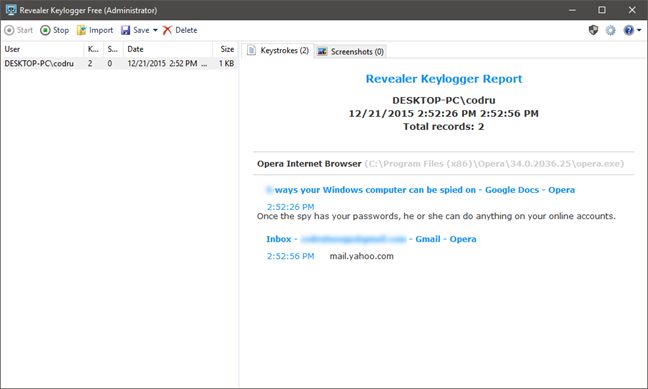
Another common spying method is to use keyloggers. These are small programs that run in the background and record every keystroke you make. Unlike remote desktop tools, keyloggers won't let your spy see what you do, nor will they give him/her access to your webcam or your computer's microphone. They are however, the best way to capture text. And by text, we mean everything: a good keylogger can capture everything you write, from the passwords you use for your online accounts to the email messages you send or the chats you make using Skype or any other chat service.
You can find plenty of keyloggers on the web and many of them are free. Here are a few of them: Revealer Keylogger Free, Spyrix Keylogger Free, Blackbox Security Monitor Express and DanuSoft Free Keylogger.
Once the spy has your passwords, he or she can do anything with your online accounts. He/she can read any email messages you received or even send email messages on your behalf.
Conclusion
Today, anyone can spy on anyone, when using the right tools. When it comes to computers and IT in general, there are countless programs that can do almost anything you might think of, in terms of spying. In this article we have only scratched the surface of this subject and revealed only the most common tools for spying on someone's Windows computer or device. If you know other types of tools and methods, don't hesitate to share them in the comments below.


 23.12.2015
23.12.2015